Hash of this article (SHA1):eeeb15caf37b08bc9a9b6058c54bc433712d748fa96e7afd80531b2531946d59
No.: Lianyuan Technology Security Knowledge No.049
Last week, we introduced GRASS's anti-witch mechanism, proxy mechanism, and the theft of Yuyue that occurred with the GRASS token issuance. After we published the article last week, we found that since GRASS became popular, there have been There are many "zero-cost" projects. Some projects have raised tens of millions of yuan, while others are just shell companies with no financing. What we are going to talk about today is a scam under the banner of a "free-for-all" project. Projects that matter.
Hang up project
Before we talk about today's topic, it is necessary to first mention some of the more well-known "hang-up projects" in the industry. These projects usually allow users to earn airdrops and token rewards through simple hang-up operations. There are many different ways of operating, but they all rely on some form of resource sharing or contribution of computing resources.
Among them, some well-known idle projects include Grass, DAWN, BlockJoker, etc. The operation mode of each project is different:
Grass: The Grass project was initially conducted through web pages, and after the second phase, it was conducted through official self-developed tools. The extra bandwidth of participants was provided to enterprises and research institutes for data transmission or network resource sharing. Bandwidth, users can get token rewards.
DAWN: Similar to Grass, DAWN is also a bandwidth sharing project, but it focuses more on providing bandwidth to homes and businesses through decentralized autonomous wireless networks, thus forming a decentralized network. Users share their network resources, Earn some rewards.
BlockJoker: This project is to hang up through the browser. By simulating the mining process in the browser, the user's computer CPU calculates the hash value, and the user performs proof of work to obtain airdrops.
The attraction of these idle projects is that most of them do not require users to perform complex operations or invest additional funds. Users can get rewards by simply letting the computer run in the background for a certain period of time. Most importantly, these rewards are usually Airdrop tokens, platform points or other forms of virtual assets, so they attract many retail users and studios to participate.
However, because these projects often promise "easy money" and "no investment", they attract a large number of retail users to participate. As we all know, where there are many people, there are scammers. Although some regular idle projects are legal However, as the popularity of these projects has increased, a large number of scams and malicious projects have also emerged.
Some of these scammers take advantage of this "hang-up" mode and pretend to be similar projects to trick users into downloading malware, browser plug-ins, or importing wallet private keys. Once users are deceived, scammers can steal their crypto assets or obtain other personal information. These criminals often disguise themselves as operators of "formal projects" and use fake success stories and social proof to increase their credibility and attract more users.
Self-developed WEB3 plug-in
The victim contacted us on November 8, telling us about his experience of being cheated in the idle project and asking for our help. The story is this: he saw someone in a Telegram group sharing a " The project owner claims that this is a completely free activity and that they have cooperated with the Nodepay project owner. As long as you use their backdoor plug-in, you can get 1.5 times the income of Nodepay's idle machine.
The people in the Telegram group that the victim joined were actively sharing their "success stories". They said that as long as the backdoor plug-in was enabled, they could get 1.5 times the profit and get more Nodepay airdrop rewards. The victim saw this information. Afterwards, he felt that it was very credible, especially when he saw that some people even posted their points growth records. The atmosphere in the group was also very lively, everyone was discussing how to earn more points, and many people recommended that he join as soon as possible. .
Under the guidance of group members (actors), the victim decided to use this backdoor plug-in, so he downloaded the backdoor plug-in and followed the steps, entering his wallet mnemonic in the backdoor plug-in. The interface of the backdoor plug-in looks normal. There was nothing suspicious about it, so the victim didn't think much about it and continued to follow the instructions.
Soon after, the victim found that the SOL and ETH assets in his wallet had been transferred away, and it was obviously stolen. Only then did he realize that he had exposed the private key of his wallet to the scammer, resulting in the loss of assets. Stolen.
After on-chain tracing analysis, we confirmed that the reason why the victim lost his assets was due to the leakage of mnemonic phrases.
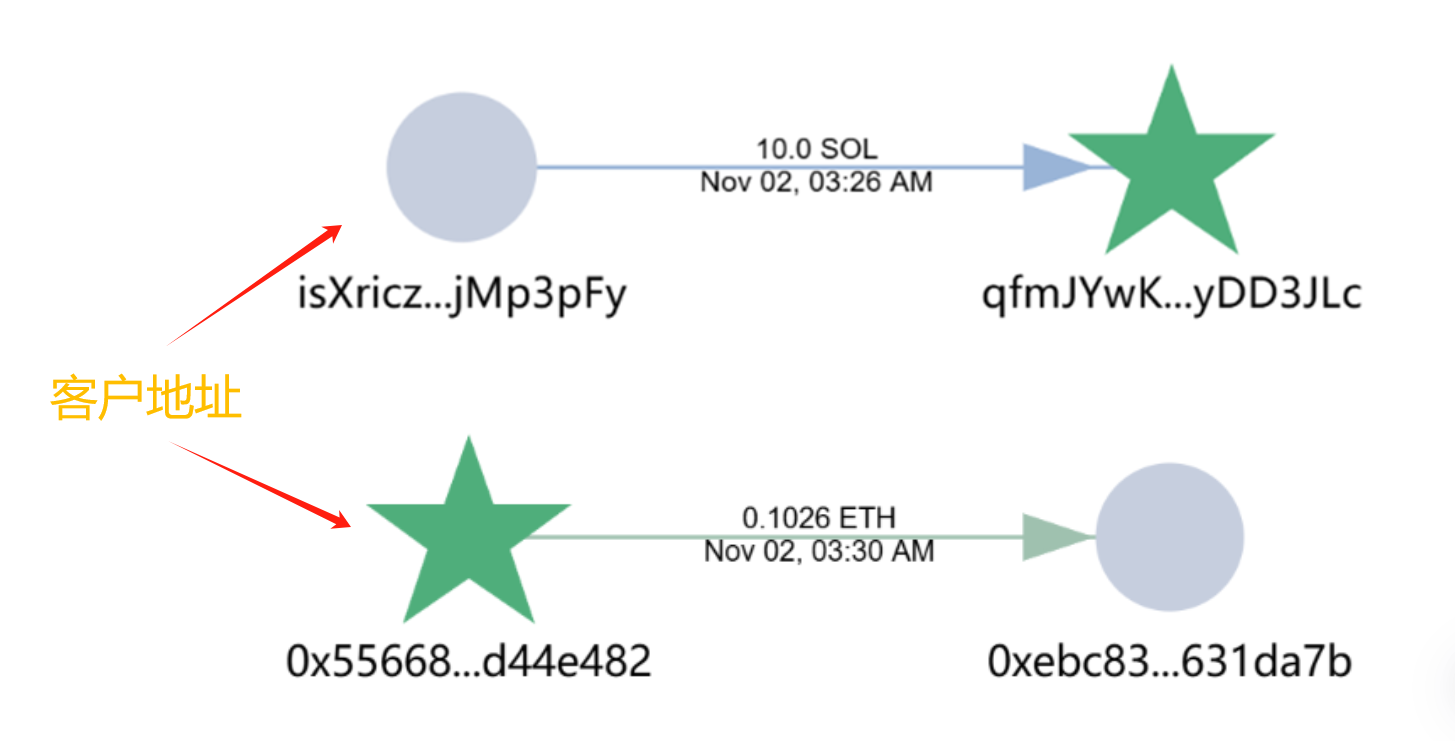
At present, the victim's assets are still stored in the scammer's address and have not changed. We are currently monitoring the two wallets and will track down the subsequent funds after they are transferred. Friends who are interested in seeing where their assets are flowing can also continue to follow us. When there are new developments, we will release them as soon as possible.
Prevention
There are so many ways to fish for idle projects, and it is a little more complicated to prevent them.
Some idle projects will require you to download backdoor tools and fill in the mnemonic words as we did above; some will directly obtain the mnemonic words stored in your mobile phone through backdoor tools; some will ask you to authorize tokens through signatures; some will Through signature, you can transfer the main chain currency, etc. In fact, the scams are still the same, just old people wearing new clothes.
So how should we prevent it?
We have summarized three don’ts for you:
First, do not disclose your mnemonic phrase. No matter what project it is, any project that requires you to fill in your mnemonic phrase is a scam.
Second, do not sign casually. Regardless of whether the signature requires GAS payment, you must confirm the specific purpose of the signature before signing;
Third, do not download backdoor tools at will. Backdoor tools may contain scripts to obtain your wallet keys. Be sure to repeatedly confirm the security of the backdoor tool and use it only after ensuring it is safe.
Conclusion
There are thousands of idle projects, and it is really difficult to get free money. Grass seems to be free money, but in fact many people or studios have spent a lot of money to build high-quality IPs to get money, because the single number income is really not much. And many projects They put in a lot of time but didn’t get a good return, and might even get a token worth about 1u. As we said in the last issue of Grass, some people not only didn’t get any income, but even lost hundreds of thousands.
So friends, please be fascinated by zero-cost and idle games. Don’t participate impulsively when you see these words. Zero-cost games not only waste your time, but sometimes may also cost you money. Please do a good job of project research before participating. Be careful about the signature of the project party, and be sure not to fill in the mnemonic phrase, and do not download application software and plug-ins at will.












